Update SSL Certificates
Valid (not self-signed) SSL certificates allow https traffic to our various sites without alarming the customer.
Universitypccare.com and other sites hosted on WHM/cPanel
All sites hosted on our cPanel server are set for automatic renewal via Let’s Encrypt. This is configured and controlled from root login to cPanel. No action should be necessary at any time, as new sites will automatically be configured for HTTPS.
Pcrt.care
Pcrt.care and its subdomains are set for automatic renewal using certbot. Renewal should happen automatically, but can be managed by logging into the server via SSH as root and running the certbot command.
There have been times where the certificate renewed, but it renewed to a different directory and so pcrt.care did not recognize the new certificate. In this case, it was necessary to find the new certificate (/etc/letsencrypt/live/) and then modify the Apache Virtual Host to point to the correct certificate path.
Adding a new subdomain
When adding a new subdomain, certbot will need to be run again to add a certificate for the subdomain. The certbot program is a guided process, so it is mostly self-explanatory.
Manage.mynet.care
This certificate is issued for the NetCare Controller. Certificate renewal is automated via Let’s Encrypt but actually applying the certificate to the Controller is not. To apply the certificate:
- Login to the RemoteCare server either via RDP or ScreenConnect.
- Run “Certify the Web” program. This is a GUI interface for issuing and renewing Let’s Encrypt certificates.
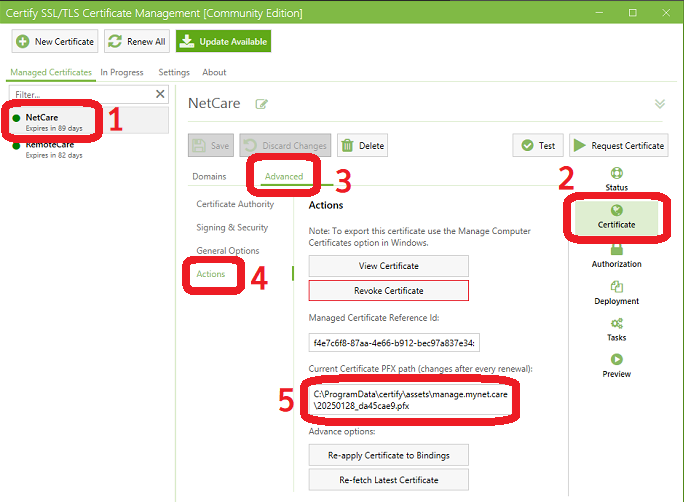
- Find the NetCare certificate in the managed certificates list on the left.
- The certificate will have already been renewed. To confirm, look at the “expires in” line underneath “NetCare” in the certificate list on the left. It should be expiring in about 90 days.
- Click on NetCare in the list on the left, then click “Certificate” on the far right and “Advanced” then “Action”. Take note of the certificate PFX path on this screen.
- See the picture below for a visual guide
- It will look something like “C:\ProgramData\Certify\certes\assets\manage.mynet.care
”.
- Open KeyStore Explorer
- Click “Open an existing KeyStore” and open “C:\Users\Administrator\Ubiquiti UniFi\data\keystore”
- Unlock the keystore file with password aircontrolenterprise.
- The expired certificate should be the only certificate in the keystore. Delete it
- Right click on an empty space in the keystore and click “Import Key Pair” (or press CTRL+K). The type of key pair to import is “PKCS #12”
- Decryption password will be blank. The file will be at the location specified in step 5 above.
- If you get an error about not being able to import the file as PKCS12, try again but use aircontrolenterprise as the decryption password.
- Click Import. When prompted, set the key pair password to aircontrolenterprise. The key should be imported and you should see it in the list with its new expiration date.
- Right click the newly imported certificate and rename it to “unifi”. You will be prompted for the aircontrolenterprise password again.
- Save the KeyStore and close KeyStore Explorer
- Open Task Manager and kill the java.exe process (this is the NetCare Controller process). It will automatically restart.
If done correctly, the next time you visit the NetCare Controller web GUI from a new tab or window you should see the new certificate with its updated expiration date.
Myremote.care
This is the certificate for ScreenConnect/Connectwise Control web interface. It is set to renew automatically via “Certify the Web” application on the RemoteCare server. The certificate is applied to the custom web server for Connectwise Control.
Mybiz.care
This is the certificate for BizCare Control Center Web Portal. It is set to renew automatically via “Certify the Web” application on the BizCare server. The certificate is applied to the default IIS site.
Apple GSX Integration
This is the certificate that allows PCRT to communicate with Apple’s GSX API. The certificate must be renewed manually each year between March 1 and March 10.
Create a Certificate Signing Request
The *passphrase *for the private key file (privatekey.pem) is in Bitwarden → University PC Care Vault → Mission Critical.
- Login to the PCRT server via SSH at
pcrt.care:2202as userupcc. - Check for existing privatekey.pem file:
ls privatekey.pem- If the key exists, continue to step 3.
- If the key does not exist, generate the private key:
openssl genrsa -aes256 -out privatekey.pem 2048using the passphrase located in Bitwarden.
- Generate a CSR based on the private key:
openssl req -new -sha256 -key privatekey.pem -out certreq.csr- When prompted for a passphrase, use the passphrase located in Bitwarden.
- Follow the prompts to generate additional data for the CSR:
- Passphrase for privatekey.pem: The passphrase located in Bitwarden.
- 2 code country letter: US
- State or province name: North-Carolina (note the dash, don’t use a space)
- Locality Name: Greenville
- Organization Name: University PC Care, Inc.
- Organizational Unit Name: leave it blank
- FQDN: AppleCare-Partner-0000706844.Prod.apple.com
- Email Address: jesse@universitypccare.com
- Challenge password: leave it blank
- Optional Company name: leave it blank
Once completed, you will have a file named certreq.csr in the current directory.
Send it to Apple
- Draft an email with the following information:
- To: gsxws@apple.com
- CC: charrell@apple.com (our Apple Manager -- they won’t process the request without this)
- Subject: Request for Certificate Renewal
- Attach: certreq.csr
- Body:
GSX Sold To account number: 706844 Primary IT contact's name: Jesse Strickland Primary IT contact's email: jesse@universitypccare.com Primary IT contact's phone number: 252-558-1280 ext 910 Static outgoing server IP address sending requests to GSX Production: 45.33.103.34 Static outgoing server IP address sending requests to GSX UT: 45.33.103.34 Apple Channel Manager: Raj Balwani CSR attached
Process and attach certificate
Apple will reply once to confirm the request has been received, then a second time to provide a download link for the certificate. The download is only good for a single download, so make sure you get all files (usually 3) and save them to a safe location. The next step should be done in Linux (such as in Windows Subsystem for Linux [WSL]):
- Run command: openssl rsa -des3 -in privatekey.pem -out privatekeyencrypted.pem
- See: https://github.com/UniversityPCCare/gsx-rest-php/issues/4
- Run command: cat Applecare-APP157-0000706844.Prod.apple.com.chain.pem privatekeyencrypted.pem > certbundle.pem
It may be possible to run the cat command in Powershell on Windows but this has not been tested yet. Then:
- Take the certbundle.pem file and use FTP to replace the existing file certificate bundle. The current file location can be found in
/var/www/pcrtv5re/vendor/gsx-rest-php/config/config.inion the pcrt.care server. - Restart httpd:
systemctl restart httpd - Load up any WO or check-in page and try to fetch details about an Apple device to confirm it is working.
Frappe Bench - ERPNext Linode
Frappe Bench hosts several sites, including hr.universitypccare.com and some customer-specific wiki sites such as ccs.docs.universitypccare.com.
Create Certificate for New Site
- Stop the NGINX web server:
sudo systemctl stop nginx - Create certificates:
sudo certbot –standalone --agree-tos --domain <domain.example.com> -n -m help@myweb.care certonly - Start the NGINX web server:
sudo systemctl start nginx - Add the following lines to
frappe-bench/sites/<domain.example.com>/site_config.json
{
"ssl_certificate": "/etc/letsencrypt/live/<domain.example.com>/fullchain.pem",
"ssl_certificate_key": "/etc/letsencrypt/live/<domain.example.com/privkey.pem"
}
- Regenerate the NGINX configuration:
bench setup nginx - Reload NGINX:
sudo service nginx reload
Renew Certificate
Certificates should automatically be renewed by LetsEncrypt, but if a manual renewal is needed, then sudo certbot renew may be enough, and if that doesn’t work, repeat steps 1-3 from Create Certificate for New Site.